
Petya Ransomware - WannaCry Deja Vu?
As we saw in May with WannaCry, the infosec community’s attention has become consumed with 'Petya', a ransomware attack targeting vulnerabilities in Windows machines. Also, as with WannaCry, these exploits originate directly from stolen US National Security Agency (NSA) files and have led to a global outbreak that is causing widespread disruption once more.
The ransomware, called NotPetya, Petrwap or a variant of Petya, has spread so quickly due in large part to a Windows-based SMB exploit called ‘Eternal Blue’. Eternal Blue was developed by the NSA to infect computers it wished to spy on. For this reason, the NSA didn't tell Microsoft about the vulnerability it had discovered in Windows until after the details had been stolen from the NSA by the ‘Shadow Brokers’ hacker syndicate. Although Microsoft has since patched this vulnerability, many organizations seem not to initiated the relevant security updates; another unfortunate similarity that facilitated the quick spread of WannaCry in May.
Petya at a Glance
Initial reports of affected computers came from government offices and energy companies in the Ukraine, including the infamous Chernobyl nuclear power plant. However, the ransomware outbreak was not confined to this region of the world, with reports of malware infections including the Spanish and Australian offices of multinational law firm DLA Piper, international shipping giant Maersk, and the Cadbury’s chocolate factory in Hobart, Tasmania, to name but a few.
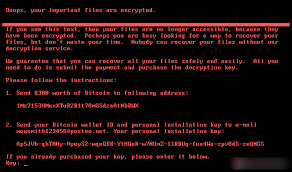
The ransom message (pictured above) states that files have been encrypted, and that a bitcoin payment worth $300 must be submitted to purchase the decryption key. This ransomware attempts to gain administrator access on infected computers; scouring memory for domain admin credentials and looking for other systems to infect within the organization.
Prevention = Technology AND Education
As we discussed here earlier this month, even when the headlines are quiet, there is a continuous barrage of emerging threats that can quickly undermine and affect an organization. Organizations need to ensure that their systems are as up to date as possible, with patches installed and secure back-ups put in place.
As an additional first line defense, CYBONET’s PineApp Mail Secure provides zero-hour threat protection by blocking email borne ransomware, preventing it from infecting your organization’s network. Click here to learn how organizations are using PineApp Mail Secure to prevent ransomware attacks originating from email; neutralizing advanced persistent threats and guarding against zero-hour viruses, malware and ransomware.
The Growing Importance of Detection Technology
With the rise of these global infections, CYBONET recognizes that 100% prevention against all the various advanced threats is not attainable. Successful campaigns, like Petya, overwhelmingly succeed due to unknowing user error, effective deception or lack of education. With the continuing evolution and scale of these threats, organizations' vulnerabilities can be exposed by even seemingly unsophisticated attacks that successfully deceive an unknowing user.
It is critical that organizations of all sizes continue to invest in preventative measures and internal security education. In parallel, it is equally important that organizations arm themselves with the ability to quickly Detect and Respond to threats within their networks. CYBONET's Cybowall solution is our newest solution, but even more, it is our recognition that prevention is not enough... LEARN MORE
Contact us at This email address is being protected from spambots. You need JavaScript enabled to view it. to learn how CYBONET is working tirelessly to put these detection and response technologies in the hands of organizations of all sizes around the world.